For my home network I’ve historically used an IPfire firewall, running on a Raspberry Pi. In general, it’s been a great little setup, however I’ve decided that I wanted to move to a beefier rig that contains both a pfSense Firewall, and a NIDS tap that feeds into a Security Onion Server, all on the same, second-hand hardware. We’re commanded to be faithful stewards of the earth, and part of that responsibility is reflected in how we deal with the resources we have. In this case, a refurbished Dell Optiplex 7050 SFF PC, with the fastest available Intel i7 (7700 – 3.6 GHz) CPU, 16 GB RAM, paired with a new, 2 TB Samsung QVO (intended for cheaper, long-term storage) and second NIC worked well, and is quite affordable. For $503, (roughly $100 cheaper than the cost of the Netgate 4100 appliance) I now have not only the pfSense Firewall, but also the benefits of Security Onion (SoS), on a relatively small-form-factor solution.
The Ansible script located here, requires that you have Ubuntu installed on the primary disk (VMs live on the 2 TB SSD), but will take care of all the rest for you. From installing and configuring the hypervisor, to the network tap, it also downloads the pfSense and SoS ISOs and leaves you with two booted VMs ready to configure. It’s also written to be safe for re-runs after completion, as it will leave completion markers on the filesystem as well as doing checks to prevent destructive operations during re-runs.
Once completed (it can take about 40 minutes to run, depending on the download speed of the ISOs), you will be able to open Virtual Machine Manager from another device and see your VMs are ready for action.
The pfSense appliance should be booted and ready for installation.
As well as the Security Onion Appliance
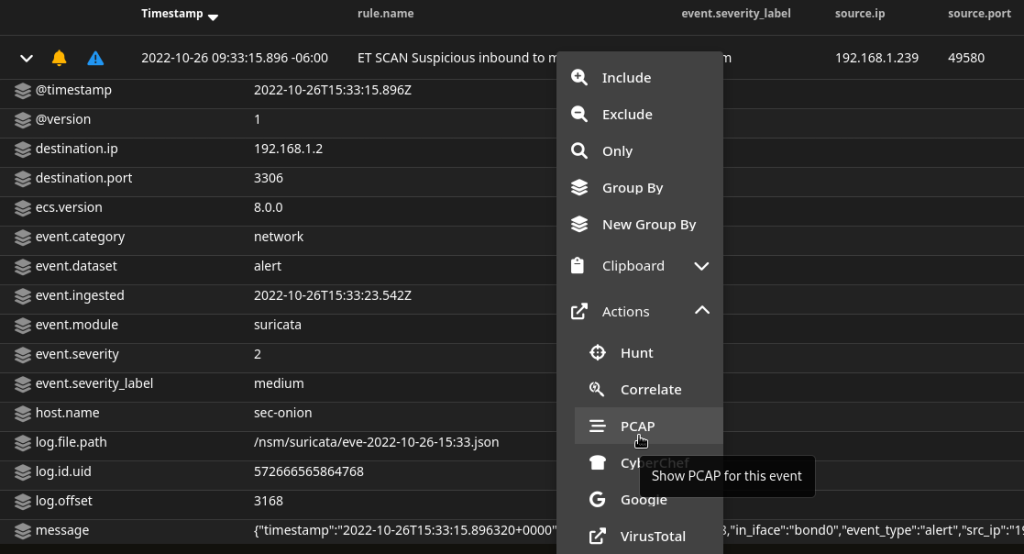
Once you have installed both appliances you should reboot the VM host to ensure that everything autostarts, and that the network tap is functioning correctly. In my case I have configured Security Onion as a Standalone Node. When running a port scan against the VM host and Firewall VM, I can see that Suricata detects the activity and raises alerts for it.
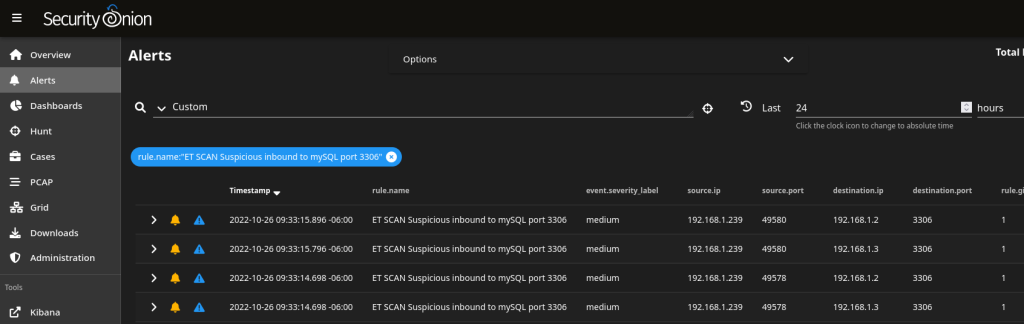
From there, the rest of Security Onion’s functionality is opened up. From event management, to the PCAP functionality, I can now view packet-level details of what this new security appliance is capturing and analyzing.